
In an era of increasing cyber threats and data breaches, safeguarding sensitive information has become paramount, especially for entities handling financial data. The Internal Revenue Service (IRS) recognizes the significance of protecting taxpayer information and has mandated the implementation of Written Information Security Plans (WISPs) for tax filers.
According to the IRS document, a security plan should be appropriate to the company’s size, scope of activities, complexity, and the sensitivity of the customer data it handles. There is no one-size-fits-all WISP. For example, a sole practitioner can use a more abbreviated and simplified plan than a 10-partner accounting firm. A good WISP should focus on three areas:
- Employee management and training
- Information systems
- Detecting and managing system failures
This article explores why WISPs are crucial, provides examples of their importance, and outlines the steps needed to ensure IRS compliance.
Why WISP or Security Policy Matters for Tax Filers, Law Firms or Accountants:
Protection Against Cyber Threats: Cybersecurity threats are ever-evolving, and tax filers are prime targets for hackers seeking to exploit financial data. A robust WISP serves as a proactive defense mechanism, helping organizations identify vulnerabilities and establish measures to mitigate potential risks.
Legal Compliance: The IRS requires tax filers to comply with various regulations and standards to safeguard taxpayer information. Implementing a WISP is not just good practice; it’s a legal requirement to ensure that businesses adhere to IRS guidelines and avoid potential penalties for non-compliance.
Preserving Client Trust: Accounting and law firms handle highly sensitive client information, including financial records and personal data. By having a comprehensive WISP in place, these businesses can demonstrate a commitment to client confidentiality and instill trust in their clients.
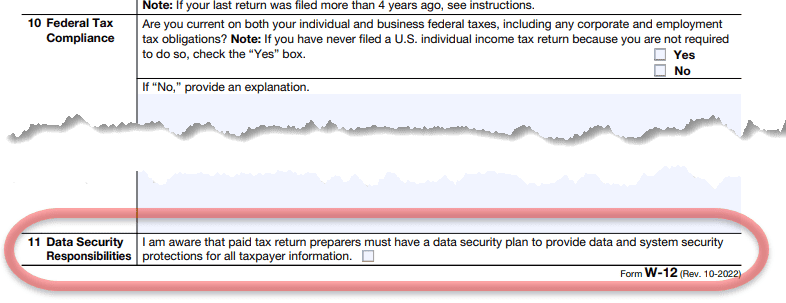
Tax Filers during the PTIN renewal process will need to sign off and check the box:
“Data Security Responsibilities: “ I am aware of my legal obligation to have a data security plan and to provide data and system security protections for all taxpayer information. Check the box to confirm you are aware of this responsibility.”
Examples of Written Information Security Plan:
-
Access Controls: Implementing strict access controls ensures that only authorized personnel can access sensitive financial data. This includes measures such as user authentication, role-based access, and encryption of stored data.
-
Regular Risk Assessments: Conducting regular risk assessments helps identify potential vulnerabilities in IT systems. By proactively addressing these weaknesses, tax filers can reduce the risk of data breaches and strengthen their overall cybersecurity posture. Learn More.
-
Employee Security Awareness Training: Human error is a common cause of data breaches. WISPs often include training programs to educate employees about cybersecurity best practices, such as recognizing phishing attempts and the proper handling of sensitive information. See an example of our security training program – Learn More.
Are you curious to know if your practice is ready for the latest FTC Safeguards requirements? It may be something you don’t think about every day, but slow outdated systems and inadequate defenses create risks and result in costly fines, downtime, and open doors for hackers or cyber criminals.
Let eSudo help you understand how well your IT infrastructure is working. We can help your business meet FTC Safeguards requirements. Start with our self-network security assessment or “PEN Test” to examine key areas of your practice:
- Test Your Network Perimeter Defense
- Are you Security Patch & Vulnerability Management current
- Discover whether you are using encryption
- Learn if your staff is using stale, repeated or crackable passwords for accounts on your network
- And much, much more.
Steps to Implement WISPs for IRS Compliance:
1. Conduct a Risk Assessment:
Identify and assess potential risks to the confidentiality, integrity, and availability of taxpayer information within your IT systems.
According to FTC Safeguard Rules:
“You can’t formulate an effective information security program until you know what information you have and where it’s stored. After completing that inventory, conduct an assessment to determine foreseeable risks and threats – internal and external – to the security, confidentiality, and integrity of customer information. Among other things, your risk assessment must be written and must include criteria for evaluating those risks and threats. Think through how customer information could be disclosed without authorization, misused, altered, or destroyed. The risks to information constantly morph and mutate, so the Safeguards Rule requires you to conduct periodic reassessments in light of changes to your operations or the emergence of new threats.”


2. Develop WISP Policies:
Create comprehensive policies that address access controls, data encryption, employee training, incident response, and other key areas of information security.
3. Employee Training and Awareness:
Ensure that all employees are well-versed in cybersecurity best practices. Regular training sessions can help reinforce the importance of WISP policies and create a security-conscious workplace culture.


4. Regular Audits and Updates:
Periodically review and update your WISP to adapt to evolving threats and changes in your IT infrastructure. Regular audits help ensure ongoing compliance with IRS regulations.
5. Incident Response Plan:
Develop a robust incident response plan to efficiently address and mitigate the impact of any security incidents. This plan should be regularly tested and updated to stay effective.

Conclusion:
In the digital age, safeguarding taxpayer information is a shared responsibility between businesses and regulatory bodies like the IRS. By implementing a comprehensive WISP, tax filers can not only meet legal requirements but also enhance their cybersecurity posture, protect sensitive data, and maintain the trust of their clients. It’s a proactive approach to ensure that IT systems are resilient against evolving cyber threats, allowing businesses to focus on their core mission of providing quality services to their clients.
Book A Call to see if we can help with WISP and compliance requirements
You may also like to take a look at some of these great resources:
Frequently Asked Questions
eSudo is a local managed IT & Cybersecurity services (MSP/MSSP) company in San Jose, CA that helps businesses make technology seamlessly work over the last 22+ years in Silicon Valley. What sets eSudo apart is we focus on security first, and computer support happens to be part of the security services.
Our team of experienced and certified computer engineers understands that no two businesses are alike, that’s why we partner with our clients to develop efficient and cost effective computer networks, cloud solutions, network security, and phone solutions that help you run your business.
As a local Microsoft Partner and Cloud Technology Specialist, eSudo has the knowledge, skills, and commitment to help you implement modern technology solutions that match your exact business needs.
Our goal is to Keep your IT Systems running and data Secure (KISS) so you can focus on running your business safely!
We specialize in working with professional service organizations like law firms, accounting firms (CPAs), and wealth management. However, eSudo have helped other business such as non-profit organizations, manufacturing and other small businesses after we have reviewed their needs and determined if they are good fit for our services.
eSudo is not a traditional computer support company; we focus on security first, and computer support happens to be part of the security services. In the dynamic landscape of network security, a proactive approach is key to safeguarding your business. It’s not a one-time event but an ongoing commitment to keep your systems resilient against evolving threats. With the rise of a mobile workforce and the omnipresence of phishing attempts or social engineering or AI, educating your employees, continuous monitoring and proactive support are vital to prevent data breaches.
If your business is looking for break-fix support or hourly IT services, we may not be for you because we cannot fully manage your risks and more importantly, it creates a trust issue in our relationship. Under a “break-fix” model, there is a fundamental conflict of interest between your business and eSudo.
“Over 97% of American businesses in 2023, operating in a digitally-driven landscape, heavily rely on the Internet for essential functions such as productivity, performance optimization, streamlined communication, bolstered sales, and various other facets of their daily operations. This heightened dependence on digital infrastructure, however, comes with a notable caveat: more than 87% of small businesses are entrusted with customer data that could be potentially compromised in the event of a cyberattack.”
We keep your IT Systems running and data secure with our proven IT Strategy, Managed Security, and Proactive Support & End User Management. Our Strategy focuses on identifying, prioritizing, and recommending the right technology for your organization. Our Managed Security includes data backup, device encryption, zero-trust access management, and policies & procedures. Our Support includes a live phone help desk, 24/7 monitoring, on-site support as needed, employee onboarding, and asset procurement.
Proven track record: We have been building our loyal customer base since 2001 in an industry where IT consulting firms come and go. Our customers, vendors, and employees stay with us because we build and value long term relationships with them. With operations all over the San Francisco Bay Area, eSudo provides reliable IT support to Northern CA-based businesses and beyond. We’re big enough to offer the facilities, services, and expertise you expect and small enough to provide the support and attention you deserve.
People & Process: Over the last 22+ years, we have created and adopted a proven process to ensure success in our operations and have trained our people to follow our proven process to provide consistent results for our customers.
Quality: We do not sell what we have not used or have tested. We recommend industrial and commercial-grade products for small businesses to provide uptime and reliability for our customers.
Responsiveness: A live person will answer your call, and emergency response time is one hour or less guaranteed. We use the most current remote support technology which lets us log in to your computers remotely to address many issues without the need to wait for a technician to come on-site.


