
. Remember this key phrase: SLAM and use this guideline to help you stay safe. When you get an email, take these simple steps, check:
- Sender: Confirm that the sender’s email address is from the correct company you ordered
- Links: Hover the URL link or website link in the message of the email to confirm it is the correct company website
- Attachment: Do not open any attachments from anyone you don’t know.
- Message: check if there is any error in the email message or misspelled domain name or company.
. If you are still not sure about individual or company that sent you an email or SMS (text message) or voice message, call the phone number on the vendor website, do not call the phone in the email, to confirm the order.
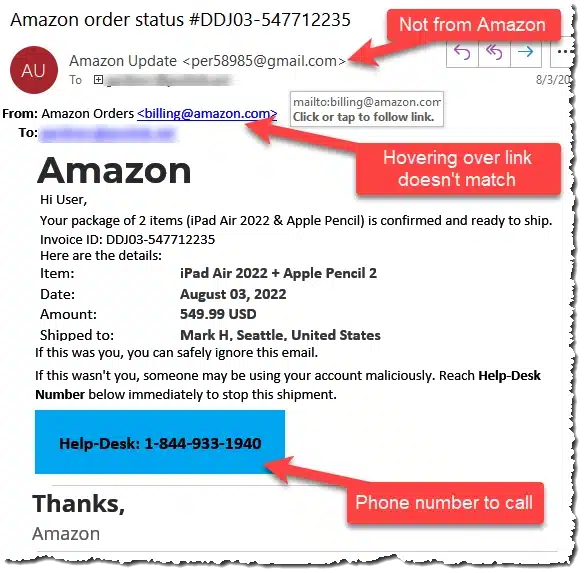
For example, this image shows a fake order which looks similar to the format you get from Amazon.
- The email is from Gmail.com, not amazaon.com
- Phone Number is not the real number on Amazon.com website.
Don’t use the same password for different sites.
Learn More – 15 ways to protect yourself.
. Confirm your devices updated to latest software version for:
- Windows 10/11 or MacOS
- Android, iPhone or iPad
- Chrome, Edge, Firefox or Safari browser
- Have security protection like anti-virus or end-point detection and response (next-gen antivirus), and a firewall.
Back up your files, photos, and email.
Encrypted any sensitive or important data (e.g., tax returns, customer information and finacial data).
Lastly, do not let anyone you don’t know remotely access your computer.
Most vendors like Amazon, Costco, Microsoft, and others will never ask to remote into your computer.
Hackers may ask to login to your computer, saying, let me verify your order or check you are safe, this is a way fro them to exploit your computer and install back door to access your computer in the future.
Don’t trust anyone you have not done business with to remote into your computer; check with your IT person or someone you know before you like someone access your computer.
Related Resource:
Top tips to protect yourself from holiday hackers – eSudo.com
Get Peace of Mind with Our Free Cybersecurity Risk Assessment! – eSudo.com
Is Your Company a Major Risk to Get Hacked? (esudo.com)
Enjoy the Holidays and Stay Safe online!


