Are you safe?
1 in 5 Small Businesses Will Suffer a Cyber Breach this Year
WHY? Cybercriminals leverage the path of least resistance.
That means businesses with limited time and resources towards cybersecurity become a prime target.
Could your business be in their sights?
Why Is Your Business at Risk?
Customer Data Makes You Vulnerable
ALL DATA IS VALUABLE TO CYBERCRIMINALS OR HACKERS BECAUSE THEY BE SOLD ON THE DARK WEB OR HOLD YOU RANSOM.
Storing and accessing customer data mixed with limited resources to dedicate to cybersecurity means your organization may be at a higher risk of suffering a cyber-attack.


92% Data Breaches due to Human Error
EMPLOYEES ARE UNAWARE OF RISKS
66% of cybercriminals rank email phishing as their attack vector of choice. Unsuspecting employees may be fooled by an illegitimate email without thinking twice.
Password Reuse is an Epidemic
IT’S EASIER TO USE AND REMEMBER ONLY ONE PASSWORD
59% of individuals admitted to mostly or always using the same password, despite 91% knowing it’s a security risk.* If a breached password is reused, the subsequent accounts are also at risk of being hacked.
(source: Lasspass by LogMein)


CEOs, CFOs or Business Owners Are Too Busy
HACKERS ARE TARGETTING BUSINESS OWNERS AND C-LEVEL EXECUTIVES TO GAIN CORPORATE ACCOUNTS 🎯
Did you know executives like you are 12 times more likely to be targeted by cybercriminals because you can access all corporate accounts and financial systems? It’s time to take action and protect yourself. You may already know this: executives like you are at higher risk of being phished, scammed, or hacked than the rest of your team.
You might say to yourself: I don’t have time for this. Would you have time to deal with a hacker impersonating you, emailing all your business contacts, friends, or teammates, and giving them ransomware?
How We Can Help Protect You!
Our clients typically have 10 to 100 workstations and rely on their computers, network, and Internet for daily operations. Most of our clients have a specialized line of business applications that they use to run their business and rely heavily on that software being operational. They represent a broad cross-section of industries (law firm, accounting, CPA, financial or wealth management, construction) across the US.
IT Strategy
- Industry-focused technology strategy for your business
- Help you to evaluate, implement and maintain the right technology to protect your organization
- Virtual CIO/CTO tailored for law firms, accountants, and financial professionals
- Proven Process to identify, prioritize and recommend the right technology business

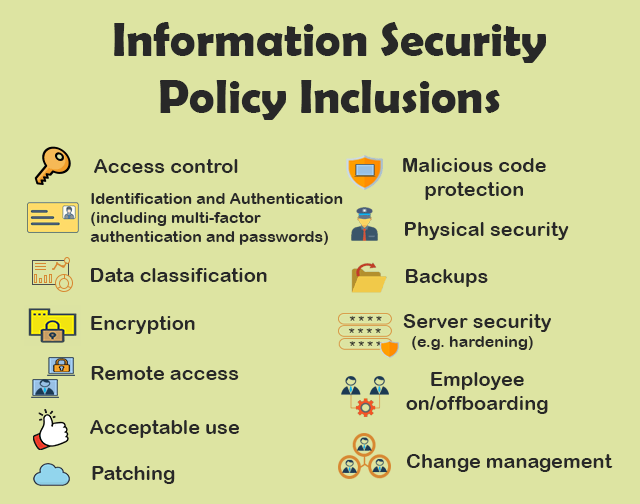
Managed Security
- Next Gen Anti-virus, Anti-malware, & Anti-phishing Email Protection
- Device Encryption & Monitoring
- Privilege Access Management with apps whitelisting (Zero-trust)
- Security Policies and Procedures
- Vulnerability Scanning & Software Updates (“Patching”)
- Backup & Disaster Recovery
- Microsoft 365 and Cloud Storage Lockdown (“Hardening”)
- Employee Onboarding and Offboarding
- Security Awareness Training
- Mobile Device Management, including personal device (BYOD)
Live Technical Support
- Live Help Desk Service
- 24/7 Monitoring of Systems
- Next Day On-site support
- Employee Onboarding and Training
- Asset Inventory
- Hardware Purchase and Management


Add our cybersecurity expert to your company's team when:
- You want a third-party looking for misconfigurations and blind spots.
- You need to prepare for Cyber Insurance requirements.
- You Demand reliability and security from your computer network.
- You know that computer downtime costs you money.
- You have compliance requirements (California Consumer Privacy Act, HIPAA, FTC Safeguards Rule for CPA/Tax Preparers) that include third-party validation or penetration tests.
- You need to educate your team on security awareness training or be certain they are doing the right thing.
- You’d like to enable your employees to work remotely.
- You believe that paying to prevent problems is more efficient than paying to fix problems.
- You’re looking for an incident and security management team with years of experience helping businesses completely recover from data breaches and cyber attacks.
This blueprint is a checklist for the business owner or decision maker to see what safeguards you need to protect yourself and data from ransomware and cyber attacks.

Frequently Asked Questions
At eSudo, we help your law firm feel like a big business when it comes to technology. Our IT services support legal practices by providing specialized solutions that align with the unique challenges and compliance needs of the legal industry. Integrating IT solutions is essential to enhance legal services, ensuring operational excellence and future growth.
For over 23+ years, we give you all the tools and support you need without the cost of hiring extra staff. That means if things go wrong, you don’t have to worry about layoffs or added expenses.
Our IT services give you the power of a large business at a fraction of the cost, helping you stay competitive in today’s digital world. With us, your business can compete with the big players and make more money while staying secure and efficient.
We specialize in working with law firms, such as estate planning, immigration and intellectual property attorneys. However, eSudo have helped other business such as non-profit organizations, manufacturing and other small businesses after we have reviewed their needs and determined if they are good fit for our services.
eSudo is not a traditional computer support company; we focus on security first, and computer support happens to be part of the security services. In the dynamic landscape of network security, a proactive approach is key to safeguarding your business. It’s not a one-time event but an ongoing commitment to keep your systems resilient against evolving threats. With the rise of a mobile workforce and the omnipresence of phishing attempts or social engineering or AI, educating your employees, continuous monitoring and proactive support are vital to prevent data breaches.
If your business is looking for break-fix support or hourly IT services, we may not be for you because we cannot fully manage your risks and more importantly, it creates a trust issue in our relationship. Under a “break-fix” model, there is a fundamental conflict of interest between your business and eSudo.
“Over 97% of American businesses in 2023, operating in a digitally-driven landscape, heavily rely on the Internet for essential functions such as productivity, performance optimization, streamlined communication, bolstered sales, and various other facets of their daily operations. This heightened dependence on digital infrastructure, however, comes with a notable caveat: more than 87% of small businesses are entrusted with customer data that could be potentially compromised in the event of a cyberattack.”
We keep your IT Systems running and data secure with our proven IT Strategy, Managed Security, and Proactive Support & End User Management. Our Strategy focuses on identifying, prioritizing, and recommending the right technology for your organization. Our Managed Security includes data backup, device encryption, zero-trust access management, and policies & procedures. Our Support includes a live phone help desk, 24/7 monitoring, on-site support as needed, employee onboarding, and asset procurement.
Proven track record: We have been building our loyal customer base since 2001 in an industry where IT consulting firms come and go. Our customers, vendors, and employees stay with us because we build and value long term relationships with them. With operations all over the San Francisco Bay Area, eSudo provides reliable IT support to Northern CA-based businesses and beyond. We’re big enough to offer the facilities, services, and expertise you expect and small enough to provide the support and attention you deserve.
People & Process: Over the last 22+ years, we have created and adopted a proven process to ensure success in our operations and have trained our people to follow our proven process to provide consistent results for our customers.
Quality: We do not sell what we have not used or have tested. We recommend industrial and commercial-grade products for small businesses to provide uptime and reliability for our customers.
Responsiveness: A live person will answer your call, and emergency response time is one hour or less guaranteed. We use the most current remote support technology which lets us log in to your computers remotely to address many issues without the need to wait for a technician to come on-site.
This is a very difficult question to answer because not all environments are the same, we will do our best to explain some general pricing guidelines.
For a business with 10 to 50 employees, IT support is a crucial investment to ensure smooth operations and data security. This support includes system maintenance, cybersecurity measures, help desk services, data backup, and software updates. As an IT manager and business owner, allocating a reasonable budget for IT support is essential to prevent downtime, protect against cyber threats, and ensure the firm’s efficiency and success in the digital era. Neglecting IT support can lead to potential vulnerabilities and higher costs in the long run. Thus, viewing IT support as a necessary investment is vital for sustaining your firm’s operations effectively and securely.
A typical price for IT Support and Cybersecurity ranges from $185 to $300 per user per month. Actual cost will be determined after we meet and perform an assessment of your environment.

