IT Support and Cybersecurity Services
Start Your Search
Services
Contact Us
Mitigate Business Risks with eSudo's Comprehensive IT Services & Security Approach
We have a team of dedicated engineers and account managers who work on your IT problems all day, every day! We offer quick response time and a certified team for a fraction of the cost of having your own IT staff.
Take a look at the managed IT Services and Cybersecurity Package we provide:
Part 1 – eSudo’s IT CARE support plan: most businesses starts with the Essential IT to keep their IT Systems Running and employees productive.
Part 2 – Advanced Cyber Protection: businesses with security requirements (e.g. cyber insurance) to keep their data secure and employees working remotely add on this component.
Part 3 – Compliance PLUS: businesses that need to comply with (California Consumer Privacy Act, HIPAA, FTC Safeguards Rule for CPA/Tax Preparers, and CMMC) would add this component to their support plan.
The diagram below provides an infographic of our support package.
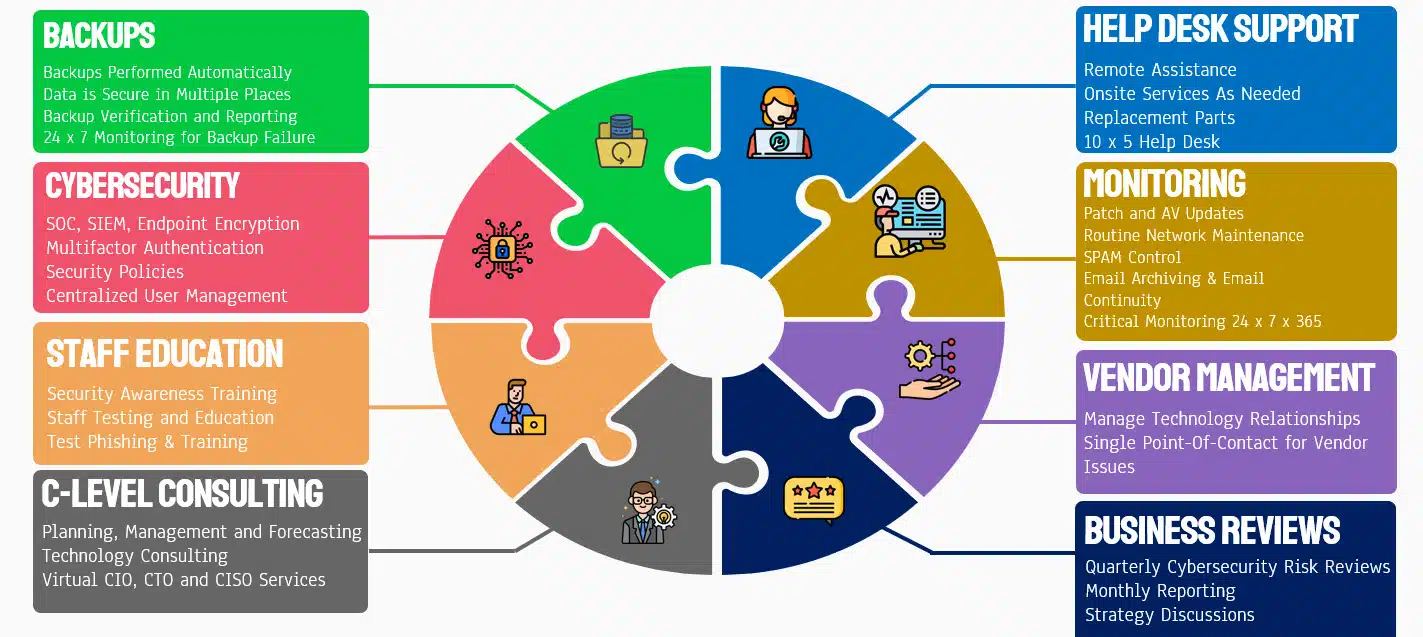
- eSudo’s IT CARE Support Plan

Most businesses starts with the Essential IT to keep their IT Systems Running and employees productive.
- Live Help Desk and Technical Support
- Unlimited Remote Support or Assistance
- Onsite Services As Needed
- After Hours & Emergency Support As Needed
- 24x7 network and critical device monitoring
- Software Patching and Security Updates for Operating Systems and Applications
- Comprehensive trouble ticket system
- Virus, Spyware scan & removal on desktops and servers
- Managed Anti-virus and anti-malware License
- Backup and Recovery Management
- Key Vendors Management
- Firewall Management
- Line of Business or Practice Management Software Support
- Device Security Policy Enforcement
- Active Directory, File Server and Cloud Storage (OneDrive, SharePoint, G-drive) Support
- Business Email, Calendar and Contacts (Microsoft 365, Google Workspace) Management
- Onsite Server or Virtual Machine (Azure, VMware, Hyper-V) Management
- Asset Tracking and Inventory Management
- Advanced Cyber Protection

Businesses with security requirements (e.g. cyber insurance) to keep their data secure and employees working remotely add on this component to IT Care Plan.
- Proactive Protection Plus
- Microsoft 365 Hardening
- Advanced Endpoint Security (next-gen anti-virus and ransomware protection) License
- Content Filtering & Reporting
- Intrusion Prevention
- Employee Security Awareness Training
- Dark-web Monitoring & Scanning
- Mobile Device Management
- Security Policies (Incident Response Plan, Disaster Recovery)
- Password Management
- Quarterly Executive Risk Review
- Compliance Plus
For HIPAA, ISO 27001, PCI, and CMMC compliances, we offer a Compliance Plus add-on that includes the following, but is not limited to.

- Policies and Procedures
- 24 x 7 Security Operations Center
- Security Expert Team On Standby
- Advanced Cyber Threat Hunting
- Machine-learning algorithms examining end user behavior, flagging irregular activity
- Network Segmentation
- Technology “cyber-sweeps”


