
This article will examine the potential for employees to inadvertently transmit sensitive company information, including W-2 forms, 1099s, or Social Security numbers, to individuals outside of the organization.
Furthermore, we will discuss strategies to safeguard your business against such human errors, thereby minimizing the risks associated with potential fines, loss of clientele, and harm to your organization’s reputation, loss of customers, and damage to your reputation.
We can discuss how to protect your sensitive data or personally identifiable information (name, address, SSN, driver’s license) using Microsoft 365 Sensitive Labels and how you can implement it yourself.
Once upon a time, in the fast-paced world of accounting, there was a diligent employee named Jen. Jen was the kind of person who could juggle client calls, spreadsheets, and coffee refills all at once—until one fateful afternoon when a single click turned into a catastrophe. ☕️📊📞
Racing against a looming tax deadline, Jen sent an urgent email containing critical client documents—W-2s, 1099s, Social Security Numbers, and more. In the rush, Jen didn’t notice that the auto-fill feature had swapped the intended recipient for someone entirely different. Whoosh—the email went to an unintended recipient with access to sensitive personal data. 📧⚠️
The fallout was immediate and severe: panicked clients, an angry boss, and the looming threat of legal trouble. The firm’s reputation, carefully built over decades, now teetered on the edge of disaster. As for Jen? Well, Jen felt like packing up and disappearing into the wilderness forever. 🌪️😟
But Jen’s firm wasn’t about to let one mistake define their future. Determined to protect their clients, reputation, and bottom line, they sought expert guidance to strengthen their cybersecurity defenses. That’s when eSudo stepped in—not as a hero, but as a trusted guide, helping the firm navigate the treacherous waters of digital security. 🛡️✨
A Plan for Prevention, Not Just Recovery
Instead of simply reacting to disasters, the firm, with eSudo’s guidance, took proactive steps to build a robust defense. Using Data Loss Prevention (DLP) and Sensitivity Labels, they created an environment where mistakes like Jen’s would be caught before they caused chaos. 🔒📋
1. Data Loss Prevention (DLP): The Firm’s Digital Safety Net
DLP became the firm’s silent guardian, scanning outgoing emails and documents for sensitive information—like Social Security Numbers or financial data. If any risky information attempted to leave the firm’s network, DLP flagged it immediately, preventing a disaster before it could unfold. 🚫💻
Even better, DLP didn’t just block mistakes; it educated employees in real-time. If Jen had tried to send that email under the new system, a friendly pop-up would have appeared: “This email contains sensitive data. Are you sure you want to send this?” That moment of pause could mean the difference between security and crisis. ⏳🔍
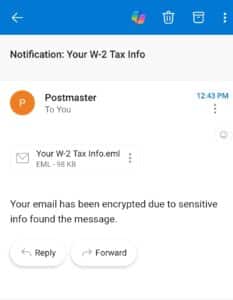
The image on the right shows the email is automatically encrypted because it is W2 or SSN information.
2. Sensitivity Labels: Ensuring Only the Right Eyes See What Matters
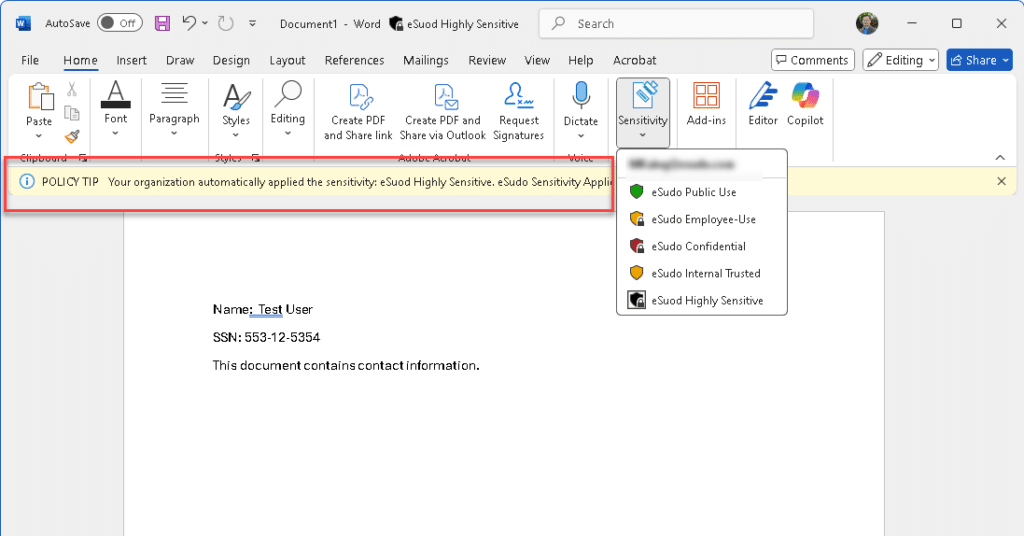
While DLP helped with outgoing communications, there was still the issue of documents stored internally or shared in the cloud. That’s where Sensitivity Labels came into play. The firm categorized files based on confidentiality levels, ensuring that only authorized individuals could access specific data. 📂🔑
For instance, a document labeled “Confidential” or “Highly Sensitive” would be automatically encrypted and restricted to a select group. Even if it was accidentally sent to the wrong person, they wouldn’t be able to open or read it. The firm wasn’t just relying on good practices—they had built-in safeguards. 🔐📄.
Winning by Protecting What Matters Most
With these solutions in place, Jen’s firm transformed from reactive to proactive. They weren’t just preventing cybersecurity disasters; they were securing their business, reputation, and profits.
- Reputation Strengthened: Clients noticed and appreciated the firm’s commitment to security, leading to greater trust and loyalty.
- Operational Efficiency: Automated security meant employees spent more time serving clients and less time worrying about mistakes.
- Financial Protection: Avoiding data breaches meant avoiding fines, lawsuits, and lost business.
- Competitive Advantage: In a world where data security is critical, the firm stood out as a leader in protecting client information.
Jen’s Journey from Crisis to Confidence
Led by the near disaster, the firm now worked with renewed confidence. 💪 While mistakes could still occur, smart security measures ensured that they wouldn’t escalate into catastrophes. 🚫💥 The firm had taken charge of its security future, with eSudo providing support at every step, delivering the tools, guidance, and expertise necessary for success. 🛠️
The key takeaway? Every business can become the hero of its own cybersecurity narrative. 🌟 With the right partner, they can safeguard their clients, protect their reputation, and maintain their profits—ensuring long-term success in an increasingly digital world. 🌐💼
Are you ready to take control of your firm’s security story? Let’s talk at https://esudo.com/booking. 📞.
eSudo is a good partner in developing and supporting long-term performance, in-office, and remote needs, cybersecurity safety, and virtual workspace to any office to the next level.


