
Do you know the biggest cybersecurity risk affecting your law firm? Are you confident that your technology is providing end-to-end security and meeting compliance? If you have a growing number of teams handling sensitive information for your practice using unprotected or unencrypted methods, then you need to act now.
Alarming statistics from Verizon’s 2021 Data Breach Investigations Report reveal that one in every five data breach victims was from a professional services organization. Furthermore, only 47% of such organizations can detect breaches within days. On average it take 225 days before the firm can detect data breach.
Learn about the steps you can take to protect your data and ensure compliance below.
Data Protection Guide to Security Challenges and Compliance Affecting Law Firms
Law firms face many security challenges in the digital age as they handle sensitive client information. From legal documents to personal data, ensuring the confidentiality and integrity of this information is paramount. Additionally, law firms must adhere to stringent regulatory requirements to protect client data and maintain trust.
Security Risks law practices face include:
- Social Engineering, including AI, Deepfake for Video & Voice
- Phishing Email
- Business Email Compromise
- Data Leak or Incidental Disclosure
- Ransomware
In this article, we’ll explore common security challenges faced by law firms and essential regulatory compliances, providing practical examples to aid consumer understanding.
- Vulnerability Scanning
- Incident Response Plan
- Security Policies
- Disaster Recovery Plan
- Security Risk Assessment
- Regulatory Compliance

1. Vulnerability Scanning
Imagine vulnerability scanning similar to going to the doctor for medical screening to ensure good health.
Vulnerability scanning involves assessing a law firm’s network and systems for potential security weaknesses. By regularly conducting vulnerability scans, law firms can identify and remediate vulnerabilities before cybercriminals exploit them. For example, a law firm might use automated scanning tools to detect outdated software versions or misconfigured settings on their servers, allowing them to patch these vulnerabilities promptly and strengthen their defenses against cyber threats.
2. Incident Response Plan
Think of an incident response plan as having a fire drill plan for your business. You need to have one before a disaster happens!
An incident response plan outlines the steps to be taken in the event of a security breach or data incident. Having a well-defined incident response plan enables law firms to respond swiftly and effectively, minimizing the impact of the incident on their clients and reputation. For instance, if a law firm’s email server is compromised, the incident response plan would detail procedures for containing the breach, notifying affected parties, and restoring affected systems from backups.

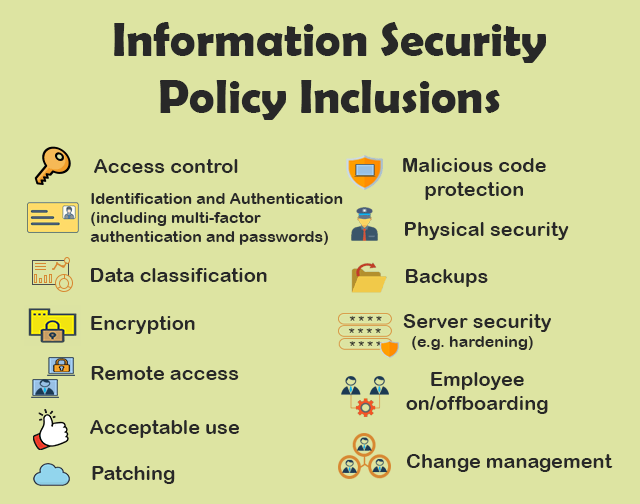
3. Information Security Policies
Information Security policies or written information security plan serve as guidelines for employees on acceptable use of technology and safeguarding sensitive information.
These policies help create a security-conscious culture within the organization and mitigate the risk of insider threats.
For example, a law firm may have policies requiring employees to use strong passwords, encrypt email communications containing confidential information, and adhere to access control measures when handling client data.
4. Disaster Recovery Plan
A disaster recovery plan outlines procedures for restoring operations during a disruptive incident, such as a natural disaster or cyberattack. Law firms can minimize downtime and ensure business continuity by having a robust disaster recovery plan. For instance, a law firm may implement regular data backups and store them securely offsite, allowing them to quickly recover critical information during a ransomware attack or server failure.


5. Security Risk Assessment
A security risk assessment involves identifying, analyzing, and prioritizing security risks faced by a law firm.
By conducting regular risk assessments, law firms can gain insights into their security posture and allocate resources effectively to mitigate potential threats. For example, a law firm might assess the risk of unauthorized access to client data and implement measures such as access controls, encryption, and employee training to reduce this risk to an acceptable level.
Risk Assessment should conducted regularly, and this can vary. It’s recommended to do it annually or when your cyber insurance policy comes up for renewal.
6. Regulatory Compliance
Law firms are subject to various regulatory requirements, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA), depending on the nature of the data they handle. Compliance with these regulations is essential to avoid legal repercussions and protect client confidentiality.
For example, a law firm handling healthcare-related cases must ensure that its data processing practices comply with HIPAA standards, including encryption of patient information and maintaining detailed audit logs.


In summary, safeguarding client data and ensuring regulatory compliance are top priorities for law firms in today’s digital landscape. With a growing rate of attacks, over 75% of businesses have been subject to these threats, often presented in the form of phishing emails and email impersonations.
By implementing robust security measures, maintaining comprehensive incident response and disaster recovery plans, and adhering to regulatory requirements, law firms can protect sensitive information and maintain the trust of their clients. Remember, investing in security today can help prevent costly data breaches and legal consequences in the future.
You may also like to take a look at some of these great resources:
- Benefits of Managed IT Services for Law Firms (esudo.com)
- Case Study – Why A Law Firm Moved To The Cloud From On-Premises Servers
- Why Is My Organization at Risk?
- Is your law firm’s technology holding you back?
- How a Law Firm Used Cloud to Scale and Work Securely?
- eSudo Blog

