
Listen to ABA & Cybersecurity Insurance Requirements for Small Law Firms
Executive Summary
In today’s digital age, small law firms, like other organizations, face an ever-increasing threat from cyberattacks. The sensitive nature of the data they handle, including confidential client information, makes them prime targets for cybercriminals. Consequently, it is crucial for these firms to understand and implement robust information technology (IT) security measures. This report outlines the key IT requirements mandated by the American Bar Association (ABA) to ensure ethical practice and the specific security controls typically required by cyber insurance providers for financial protection. By adhering to these guidelines and implementing the necessary safeguards, small law firms can not only avoid ethical violations and potential disciplinary actions but also secure adequate cyber insurance coverage, thereby protecting their firm’s and their clients’ best interests. The focus will be on providing actionable insights and practical recommendations tailored to the needs and resources of law firms with 10 to 30 employees.
II. Introduction: The Heightened Cybersecurity Landscape for Small Law Firms:
The legal industry, including small law firms, is experiencing a significant surge in cyber threats, with a notable percentage of firms having encountered security breaches. These threats are becoming more frequent and sophisticated, posing considerable risks to the sensitive information entrusted to legal professionals. Statistics indicate that a substantial portion of law firms, regardless of their size, have been victims of cyber incidents, underscoring the pervasive nature of this challenge.Small law firms are particularly attractive targets for cybercriminals due to the valuable information they possess. This includes trade secrets, intellectual property, personally identifiable information (PII), and confidential attorney-client privileged data. Furthermore, some law firms may also have access to client trust accounts, making them susceptible to financial theft and ransom demands. Compared to larger firms, smaller practices might have fewer resources dedicated to implementing and maintaining comprehensive cybersecurity measures, potentially making them easier targets for malicious actors.

Given this landscape, it is of paramount importance for small law firms to address cybersecurity proactively. This involves a two-pronged approach: first, adhering to the ethical guidelines established by the ABA, which now explicitly include technology competence and the duty to protect client confidentiality in the digital realm; and second, meeting the specific security requirements set forth by cyber insurance providers. Compliance with both is essential. The ABA’s guidelines help ensure that legal professionals uphold their ethical obligations to clients, while cyber insurance offers crucial financial protection in the event of a data breach or other cyber incident. By understanding and implementing the necessary IT security measures, small law firms can safeguard their operations, maintain client trust, and secure their financial future in an increasingly perilous digital environment.
III. ABA's Requirements for Law Firm IT
The American Bar Association (ABA) sets forth ethical guidelines that all lawyers should follow. These guidelines have evolved to address the increasing role of technology in the practice of law and the associated cybersecurity risks. Several Model Rules of Professional Conduct and Formal Opinions provide specific guidance relevant to law firm IT.
A. Ethical Obligations:
ABA Model Rule 1.1, concerning competence, mandates that lawyers provide competent representation to their clients. This includes possessing the legal knowledge, skill, thoroughness, and preparation reasonably necessary for the representation. Recognizing the integral role of technology in modern legal practice, Comment 8 to this rule was amended in 2012 to explicitly state that a competent lawyer should keep abreast of changes in the law and its practice, including the benefits and risks associated with relevant technology. This obligation is not static; it requires ongoing learning and adaptation as technology evolves. This duty of technological competence applies to all aspects of a law practice, including virtual practices, where lawyers must understand the ethical issues and risks associated with their particular areas of practice to choose and manage technologies effectively. Therefore, small law firms must ensure that their attorneys and staff possess a reasonable understanding of the technologies they use, including the inherent security risks and available safeguards.ABA Model Rule 1.6 addresses the confidentiality of information relating to the representation of a client. This rule generally prohibits lawyers from revealing such information unless the client gives informed consent or the disclosure is impliedly authorized or permitted by other provisions of the rule. Crucially, paragraph (c) of Rule 1.6 explicitly states that a lawyer shall make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client. This requirement directly applies to the use of technology in legal practice. Small law firms must implement appropriate security measures to protect client information stored and transmitted electronically, ensuring that only authorized individuals have access and that data is protected from breaches. The duty to maintain confidentiality is a cornerstone of the attorney-client relationship, and in the digital age, it necessitates a proactive approach to data security.ABA Model Rule 1.4 outlines a lawyer’s duty to communicate with their clients. This rule requires lawyers to keep clients reasonably informed about the status of their matter and to explain matters to the extent reasonably necessary to permit the client to make informed decisions regarding the representation. This obligation extends to informing clients about the use of technology in their representation, particularly when generative artificial intelligence (AI) tools are employed. Furthermore, in the event of a data breach that involves or has a substantial likelihood of involving material client information, lawyers have a duty to notify current clients of the breach. This notification must be timely and provide sufficient information to allow the client to understand the situation and make informed decisions regarding their representation. Therefore, small law firms need to establish clear communication protocols for informing clients about technology use and any security incidents that may affect their confidential information.
B. Formal Opinions and Resolutions:
The ABA has issued several Formal Opinions that provide further guidance on the ethical obligations of lawyers concerning technology and cybersecurity. Formal Opinion 477R, titled “Securing Communication of Protected Client Information,” specifically addresses the use of electronic communications. This opinion emphasizes that lawyers must make “reasonable efforts” to ensure that their client communications are secure, especially when transmitting information over the internet, including email. What constitutes a reasonable effort is not a fixed rule but rather a flexible set of factors to be weighed on a case-by-case basis, including the sensitivity of the information, the likelihood of disclosure without additional safeguards, the cost and difficulty of implementing safeguards, and the extent to which safeguards might adversely affect the lawyer’s ability to represent clients. The opinion suggests that in certain circumstances, particularly when dealing with highly sensitive information, lawyers may be required to use encryption to secure email communications. Small law firms should assess the sensitivity of their client data and consider implementing encryption for electronic communications where appropriate.ABA Formal Opinion 483, “Lawyers’ Obligations After an Electronic Data Breach or Cyberattack,” provides a roadmap for a lawyer’s ethical obligations following a data breach involving confidential client information. This opinion emphasizes that lawyers have a duty to employ reasonable efforts to monitor their technology and office resources for breaches. Once a breach occurs, lawyers must act reasonably and promptly to stop the breach and mitigate any resulting damage. This includes having an incident response plan in place to address the situation in a coordinated manner. The opinion also clarifies the duty to notify clients of a data breach, stating that an obligation exists to communicate with current clients if material client confidential information is misappropriated, destroyed, or otherwise compromised, or if the lawyer’s ability to perform legal services is significantly impaired. Small law firms should develop a comprehensive incident response plan that outlines the steps to take in the event of a cyberattack, including procedures for assessment, containment, communication, documentation, and mitigation.ABA Formal Opinion 498, “General Guidance for Virtual Law Practices,” addresses the ethical considerations for lawyers practicing virtually. This opinion applies the well-established principles of technology competence, confidentiality, and supervision to the context of virtual practice. It emphasizes that lawyers with a virtual practice must continue to understand the ethical issues and risks at play in their specific areas of practice to choose and manage technologies that aid such practices without creating undue risk. The opinion provides guidance on the use of various hardware and software commonly used in virtual practices, such as virtual meeting platforms, remote document access platforms, and virtual assistants, highlighting the need to ensure confidentiality and data security in these environments.
Small law firms with remote or hybrid work arrangements should review this opinion to ensure they are addressing the specific security challenges associated with virtual practice. ABA Formal Opinion 512, “Ethics Guidance on a Lawyer’s Use of AI Tools,” provides the first formal opinion from the ABA on the ethical implications of using generative artificial intelligence (AI) in the practice of law. This opinion emphasizes that lawyers using AI tools must fully consider their applicable ethical obligations, including the duties to provide competent legal representation, protect client information, communicate with clients, and charge reasonable fees. Regarding competence, lawyers must have a reasonable understanding of the capabilities and limitations of the specific AI technology they use. When it comes to confidentiality, lawyers must assess the risks associated with the potential disclosure of client information when using AI tools and may need to obtain the client’s informed consent before entering any confidential information into a third-party generative AI program. The opinion also addresses the duty to communicate, noting that lawyers must disclose their use of AI tools to clients under certain circumstances, such as when asked or when it affects fees. Small law firms considering or currently using AI tools should carefully review this opinion to ensure they are adhering to their ethical responsibilities in this rapidly evolving technological landscape.Beyond Formal Opinions, the ABA has also issued Resolutions addressing cybersecurity and AI. Resolution 112 (2019) urges courts and lawyers to address the emerging ethical and legal issues related to AI usage. Resolution 700 (2022) concerns the use of pretrial risk assessment tools. Resolution 604 (2023) urges organizations that design, develop, deploy, and use AI systems to follow several guidelines related to bias, accountability, and transparency. More recently, Resolution 609 urges lawyers to keep abreast of new technologies, enhance their cybersecurity protections, be vigilant with third-party vendors, and advise clients on their cyber defenses. Resolution 109 encourages all firms to develop, implement, and maintain an appropriate cybersecurity program. These resolutions reflect the ABA’s ongoing efforts to guide the legal profession in navigating the complex ethical and security challenges presented by technological advancements.
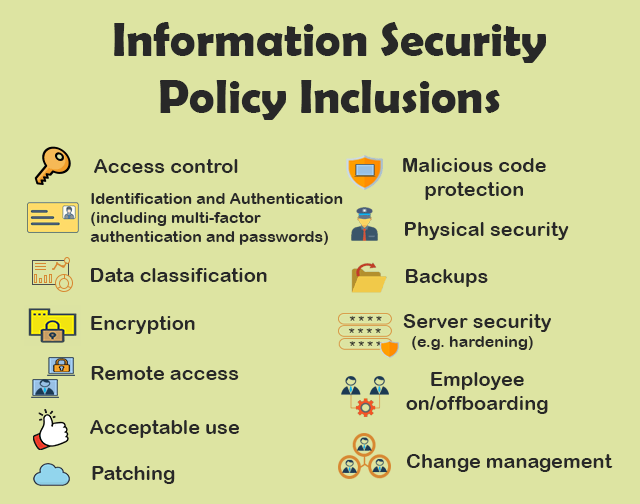
The ABA provides several practical recommendations for law firms to enhance their IT security. Developing robust policies regarding the use of technology by staff is crucial. These policies should include backup and disaster recovery plans and security procedures for protecting client and case data consistent with the duty of confidentiality. For virtual practices, managerial lawyers must adopt and tailor policies to ensure ethical conduct by subordinates, especially when using personal devices for work, including remote-wiping capabilities and data archiving. The ABA emphasizes the increasing importance of technology policies, with a growing number of law firms implementing them, covering areas such as email use, acceptable computer and internet use, remote access, and disaster recovery/business continuity. Small law firms should prioritize the creation and regular review of comprehensive technology policies tailored to their specific operations.Data encryption is another key security measure recommended by the ABA to protect client data. This involves transforming information into an unreadable format, making it incomprehensible to unauthorized individuals. Encryption should be used both when data is stored (at rest) and when it is being transmitted (in transit), especially for sensitive client information. While the adoption of encryption is increasing among law firms, it is still not universally implemented. Small law firms should adopt encryption technologies for their sensitive data and electronic communications to ensure confidentiality.Regular staff training on cybersecurity is also strongly recommended by the ABA. Human error is a significant factor in many data breaches, making it essential to educate all firm personnel about potential threats such as phishing attacks, malware, and social engineering. Training should cover topics like creating strong passwords, identifying suspicious emails, safely browsing the internet, and adhering to the firm’s security policies. Some cyber insurance carriers may even require cybersecurity awareness training for employees. Small law firms should implement regular cybersecurity training programs for all employees and ensure that this training is updated to address new and evolving threats.Backup and disaster recovery plans are critical for ensuring business continuity in the event of a cyberattack or other disruptive event. Regular data backups ensure that the firm can restore its systems and data if they are compromised or lost. Disaster recovery plans outline the procedures for resuming operations after a disruption. While many law firms have disaster recovery policies, it is essential to ensure these plans are robust and regularly tested. Small law firms should establish comprehensive backup and disaster recovery plans that include offsite storage of backups and regular testing of the restoration process.Finally, the ABA recommends that law firms carefully vet third-party vendors who provide IT services or have access to client data. Many data breaches occur through vulnerabilities in third-party systems, making it crucial to conduct due diligence to assess the vendor’s security practices. This includes reviewing their cybersecurity credentials, auditing their security policies, and ensuring that contracts include clauses regarding data protection and breach notification. Small law firms should implement a process for vetting and managing their third-party vendors to minimize the risk of security breaches.
IV. Cyber Insurance Requirements for Law Firm IT

Given the increasing cyber threats and the potential for significant financial losses, cyber insurance has become a crucial component of risk management for law firms, including small practices. While not always legally mandated, cyber insurance can provide essential financial protection against the costs associated with data breaches and other cyber incidents.
A. The Necessity of Cyber Insurance:
Cyber insurance is increasingly considered essential for law firms due to the inherent cyber risks of handling sensitive electronic data. Even if not legally required, obtaining cyber insurance is a prudent step for small law firms to mitigate potential financial losses and legal liabilities arising from cyberattacks. While crucial for malpractice claims, legal professional liability (LPL) insurance may not cover all the costs associated with a cyber breach, such as data recovery, notification expenses, and business interruption, making dedicated cyber insurance necessary. Cyber insurance acts as a powerful risk management tool, providing financial coverage to help firms recover from costly data breaches, ransomware attacks, and other malicious incidents. The rising frequency and severity of cyberattacks have made cyber insurance more important than ever for law firms seeking to protect their financial stability and reputation.The financial impacts of cyberattacks on law firms can be substantial and multifaceted. First-party coverage in cyber insurance policies can help protect against monetary losses due to lost, damaged, or stolen data, covering recovery costs. It may also cover loss of income resulting from business interruption caused by a cyber incident and expenses related to cyber extortion, such as ransom payments. Notification costs are typically covered, including expenses incurred when informing affected parties about a data breach. Some policies may also provide coverage for reputational damage, including public relations and marketing costs to help restore the firm’s image. Additionally, crisis management expenses, such as hiring IT specialists, forensic accountants, lawyers, or PR experts to assess the damage and mitigate the loss, may be included. Beyond these direct costs, cyberattacks can lead to liability to third parties, triggering regulatory investigations and legal action from affected clients. Cyber insurance can provide third-party coverage for network security and privacy liability, helping to cover claims against the firm for negligently failing to protect confidential personal data. It may also cover expenses related to regulatory proceedings and electronic media liability, such as lawsuits for libel or defamation resulting from a data breach. Small law firms need to be aware of the wide range of potential financial repercussions of a cyberattack and ensure their cyber insurance policy provides adequate coverage for these risks.
B. Common Security Controls Mandated by Insurers:
Cyber insurance providers typically have specific security controls that law firms must implement to be eligible for coverage or to secure more favorable rates. One of the most common and critical requirements is the implementation of Multi-Factor Authentication (MFA) for all remote access, including email. MFA adds an extra layer of security by requiring users to provide two or more verification factors to access their accounts, making it significantly harder for unauthorized individuals to gain entry even if they have stolen passwords. Insurers view MFA as a fundamental security control to prevent unauthorized logins and protect sensitive data.Another common requirement is the deployment of Endpoint Detection and Response (EDR) or Antivirus software on all user devices. This software is designed to detect and prevent malware, ransomware, and other malicious threats from compromising the firm’s computers and networks. Regular updates and maintenance of this software are also typically mandated by insurance providers to ensure its effectiveness against the latest cyber threats.Maintaining regular and reliable data backups is also a near-universal requirement for cyber insurance.
In the event of a cyberattack, especially a ransomware incident, having up-to-date backups allows the firm to restore its data and systems without having to pay a ransom. Insurers want to ensure that policyholders have a robust data recovery plan in place to minimize potential losses.Security awareness training for employees is another essential security control often mandated by cyber insurance providers. Since a significant percentage of data breaches are caused by human error, insurers recognize the importance of educating employees about cybersecurity threats like phishing and social engineering. Regular training helps employees identify and avoid these threats, reducing the firm’s overall risk.Having a well-defined and tested Incident Response Plan (IRP) is also a common requirement. An IRP outlines the procedures and steps the firm will take in the event of a cyber incident, ensuring a swift and effective response to minimize damage and downtime. Insurers want to see that policyholders are prepared to handle security incidents in a timely and organized manner.In addition to these core requirements, cyber insurance providers may also mandate other security measures such as properly configured firewalls to control network traffic, strong password policies that require complex and frequently changed passwords, strict access management controls based on the principle of least privilege (granting users only the necessary access to perform their job duties), and data classification to ensure that sensitive information receives the appropriate level of protection. Small law firms should be prepared to demonstrate that they have implemented these and other relevant security controls to meet the requirements of cyber insurance providers and secure adequate coverage.
C. Policy Coverage and Considerations:
When selecting a cyber insurance policy, small law firms should understand the different types of coverage available. Cyber insurance policies typically offer both first-party and third-party coverage. First-party coverage protects the law firm directly for its own losses incurred due to a cyber incident. This can include expenses for data recovery, business interruption, crisis management, forensic investigations, notification costs, and cyber extortion. Third-party coverage, on the other hand, protects the law firm from liability claims made against it by others, such as clients, due to a data breach. This can cover legal defense costs, settlements, and regulatory fines. Law firms can opt for either type of coverage or a combination of both, depending on their specific needs and risk assessment.Several key factors should be considered when selecting a cyber insurance policy. Coverage limits are crucial; the firm should choose a policy with limits that are sufficient to cover potential losses, which can vary depending on the size of the firm and the sensitivity of the data handled. Exclusions in the policy should be carefully reviewed to understand what types of incidents or losses are not covered. Deductibles, the amount the firm must pay out-of-pocket before the insurance coverage kicks in, should also be considered in relation to the firm’s budget. It is also important to assess the insurer’s expertise and experience in handling cyber claims for law firms, as this can significantly impact the claims process and outcome. Small law firms may also want to check if their existing professional liability policies offer any data breach coverage, although dedicated cyber insurance typically provides more comprehensive protection. Consulting with other attorneys and working with an insurance provider who specializes in cyber security insurance for law firms can also be beneficial in selecting the right policy.
D. Impact of Security Posture on Premiums and Eligibility:
A law firm’s IT security measures have a direct impact on the cost and availability of cyber insurance. Insurers assess the firm’s security posture to determine the level of risk they are undertaking by providing coverage. Law firms that have implemented robust cybersecurity measures, such as MFA, EDR/Antivirus, regular backups, employee training, and an incident response plan, are generally considered lower risk. This lower risk can translate into lower insurance premiums and better eligibility for coverage. Conversely, law firms with weak or inadequate security practices may be seen as higher risk, potentially leading to higher premiums, limited coverage options, or even denial of coverage. Therefore, investing in and maintaining a strong IT security posture is not only essential for protecting the firm and its clients but also for securing affordable and comprehensive cyber insurance coverage.
V. Aligning ABA Requirements and Cyber Insurance Demands
For small law firms, understanding the alignment between the ABA’s ethical obligations and the security requirements of cyber insurance providers is crucial for efficient and effective implementation of IT security measures.
A. Overlapping Areas:
There is a significant overlap between the ABA’s ethical focus on protecting sensitive client data and cyber insurance providers’ goal of mitigating financial risks associated with data breaches. Both entities emphasize the fundamental importance of safeguarding client information from unauthorized access and disclosure. Consequently, many of the recommended and required security measures align directly. For instance, the ABA’s emphasis on the duty of competence in technology and the duty to maintain confidentiality in the digital age naturally leads to the recommendation and requirement of robust data protection measures, which are also central to cyber insurance.Several specific security practices are highlighted by both the ABA and cyber insurance providers. The ABA’s call for security procedures for protecting client data aligns with cyber insurers’ focus on data protection as a primary concern. Similarly, the need for regular risk assessments, whether to understand technology risks as per ABA guidelines or to identify vulnerabilities for insurance purposes, is a shared area of focus. Employee training on cybersecurity is also crucial for both ethical compliance (ensuring competence and preventing breaches due to human error) and meeting insurance requirements (as insurers recognize the human factor in security incidents). Furthermore, the establishment of an incident response plan is vital for adhering to ABA guidelines on responding to data breaches and is also a standard requirement for most cyber insurance policies. These overlapping areas indicate that by focusing on these core security practices, small law firms can simultaneously work towards meeting their ethical obligations and securing adequate cyber insurance coverage.
Reference: Ensuring Security: Protecting Your Law Firm and Client Data
- B. Potential Differences:
While the overarching goals of the ABA and cyber insurance providers are aligned, there can be potential differences in their specific focus and requirements. The ABA’s guidelines tend to be broader, focusing on the ethical principles of competence and confidentiality, and may not always specify the exact technical controls required. For example, while the ABA emphasizes the need for reasonable security measures, cyber insurance providers often have more granular and technically specific mandates, such as requiring a particular type of encryption or a specific frequency for software patching. Additionally, compliance with legal statutes like HIPAA, while important, does not automatically equate to compliance with the ABA’s ethical obligations. Cyber insurers, in their risk assessment, may place a greater emphasis on the implementation of specific security programs and technologies to quantify and manage risk effectively. Therefore, small law firms should be aware that while adhering to ABA principles is essential, they may also need to meet more detailed technical requirements to satisfy cyber insurance providers.
- C. Strategies for Comprehensive Compliance:
To achieve comprehensive compliance with both ABA requirements and cyber insurance demands, small law firms should adopt a holistic approach to IT security. This involves understanding the core ethical principles outlined by the ABA and then implementing the specific technical and organizational controls often mandated by cyber insurers. Developing a comprehensive data security policy that addresses both ethical considerations and insurance requirements is a crucial first step. This policy should cover areas such as data handling, access controls, employee responsibilities, and incident response. Implementing essential technical safeguards like MFA, encryption, firewalls, and intrusion detection systems, as often required by insurers, will also help meet the ABA’s expectation of reasonable security measures. Regular cybersecurity awareness training for all staff members is vital for both preventing breaches (aligning with ethical duties) and satisfying insurance requirements. Establishing and regularly testing a robust incident response plan is also critical for both ethical compliance in the event of a breach and meeting insurance mandates. Finally, carefully vetting and managing third-party vendors, as recommended by the ABA and often scrutinized by insurers, is essential for maintaining a secure IT environment. By integrating these strategies, small law firms can build a resilient and compliant IT framework that addresses both their ethical obligations and their need for cyber insurance protection.
VI. Practical Implementation for Small Law Firms (10-30 Employees)
For small law firms with 10 to 30 employees, implementing the necessary IT security measures to meet ABA and cyber insurance requirements can seem daunting. However, by focusing on key areas and adopting practical strategies, these firms can build a robust security framework.
A. Developing a Tailored Cybersecurity Policy:
Creating a comprehensive yet manageable cybersecurity policy is a fundamental step for small law firms. This policy should be tailored to the firm’s specific operations, size, and the types of data it handles. It should clearly outline acceptable use of firm devices and applications, protocols for storing, sharing, and deleting client files, procedures for responding to unauthorized disclosures or potential data breaches, and minimum standards for access control and encryption. The policy should also include guidelines for email and computer use, remote access, and social media, ensuring that all employees understand their responsibilities in maintaining the firm’s security. It is crucial to make the policy easy to understand and follow for all staff members. Regularly reviewing and updating the policy to reflect changes in technology and threats is also essential to maintain its relevance and effectiveness.
B. Implementing Essential Technical Safeguards:
Deploying key security technologies is crucial for protecting a small law firm’s IT infrastructure and data. Multi-Factor Authentication (MFA) should be implemented for all user accounts, especially those with access to sensitive client data and for remote access to the firm’s network. Data encryption should be applied to all sensitive data both when it is stored on the firm’s systems and when it is transmitted electronically, such as via email. A properly configured firewall is essential to control network traffic, blocking unauthorized access and malicious connections. While a full intrusion detection system might be complex for a small firm to manage, basic measures like enabling logging and monitoring network activity can help detect suspicious behavior. Small law firms should prioritize these essential technical safeguards to create a strong security foundation.
C. Conducting Effective Employee Training:
Regular cybersecurity awareness training for all staff members is paramount for preventing data breaches in small law firms. Training sessions should educate employees about common threats such as phishing emails, malware, and social engineering tactics, and provide them with the knowledge to recognize and avoid these threats. The training should also cover the firm’s cybersecurity policies and procedures, including guidelines for password creation, data handling, and reporting suspicious activity. It is important to make the training engaging and relevant to the employees’ daily tasks. Regular reminders and updates on emerging threats can also help reinforce security best practices. Small law firms can utilize online training resources, webinars, or even bring in external experts to conduct training sessions for their staff.Establishing an Incident Response Plan:
Creating and testing a data breach incident response plan is a critical step for small law firms to prepare for and manage potential cyber incidents. The plan should outline the specific steps to be taken in the event of a suspected or confirmed data breach. This includes procedures for assessing the scope of the breach, containing the incident to prevent further damage, communicating with affected parties (including clients and regulatory bodies if required), documenting the incident and the response, and taking steps to mitigate the impact and prevent future occurrences. The plan should also identify key personnel who will be responsible for different aspects of the response, such as an incident lead, IT support, and potentially legal counsel and a public relations representative. Regularly testing the incident response plan through simulated scenarios can help identify any weaknesses and ensure that all team members know their roles and responsibilities in the event of a real incident.E. Managing Third-Party Vendors:
Small law firms often rely on third-party vendors for various IT services, making it essential to carefully vet and manage their security practices. Before engaging a vendor, the firm should conduct due diligence to assess their cybersecurity credentials and ensure they have adequate security measures in place to protect the firm’s and its clients’ data. This may involve reviewing the vendor’s security policies, certifications, and past security incidents. The firm should also ensure that contracts with third-party vendors include clear clauses regarding data protection, confidentiality, and breach notification responsibilities. Regularly reviewing the vendor’s security practices and monitoring their compliance with contractual obligations is also important to mitigate the risk of a data breach occurring through a third-party system.

VII. Consequences of Non-Compliance
Failure to adhere to the ABA’s ethical guidelines and to meet the security requirements of cyber insurance providers can have significant negative consequences for small law firms.
A. Ethical and Disciplinary Ramifications:
Inadequate data security practices can lead to serious ethical and disciplinary ramifications for lawyers and law firms. Failing to implement reasonable measures to protect client confidentiality, as mandated by ABA Model Rule 1.6, can result in ethics violations and disciplinary actions by state bar associations. Additionally, if a data breach occurs due to a lack of reasonable security efforts, it can be considered a breach of the duty of competence under Model Rule 1.1. Clients who suffer harm as a result of a law firm’s data breach may also have grounds for legal malpractice claims, leading to financial liabilities and damage to the firm’s reputation. Therefore, prioritizing data security is not only an ethical imperative but also a crucial aspect of risk management for small law firms.
B. Insurance Claim Denials and Financial Losses:
Failing to meet the specific security requirements outlined in a cyber insurance policy can result in the denial of claims in the event of a cyber incident. Cyber insurance policies often contain clauses that require policyholders to maintain certain minimum security standards. If a claim arises from a cyberattack and the insurer determines that the law firm did not have the required security controls in place at the time of the incident, the claim may be denied. This can leave the small law firm to bear the full financial burden of the cyber incident, which can include significant costs for data recovery, legal fees, regulatory fines, business interruption losses, and reputational damage. Therefore, it is crucial for small law firms to not only obtain cyber insurance but also to ensure they fully understand and comply with all the security requirements specified in their policy to avoid potential claim denials and significant financial losses
VIII. Conclusion: Building a Resilient and Compliant IT Framework
In conclusion, the imperative for small law firms to prioritize IT security has never been greater. By understanding and diligently implementing the requirements set forth by both the ABA and cyber insurance providers, these firms can navigate the complex cybersecurity landscape effectively. Adhering to the ABA’s ethical guidelines, which emphasize technology competence and the protection of client confidentiality, forms the bedrock of responsible legal practice in the digital age. Simultaneously, meeting the specific security controls mandated by cyber insurance providers is essential for securing the financial safeguards necessary to mitigate the potentially devastating costs of a data breach or cyberattack.
The overlapping nature of these requirements means that investments in core security practices, such as developing tailored cybersecurity policies, implementing essential technical safeguards like MFA and encryption, conducting regular employee training, establishing robust incident response plans, and carefully managing third-party vendors, will serve the dual purpose of ensuring ethical compliance and enhancing insurability. While the ABA’s focus may be on broader ethical principles and cyber insurers may have more technically specific demands, the ultimate goal is shared: the protection of sensitive data and the minimization of risks.
For small law firms, building a resilient and compliant IT framework is not merely about avoiding negative consequences like disciplinary actions or denied insurance claims. It is also about fostering trust with clients, safeguarding their confidential information, and ensuring the long-term viability and success of the firm in an increasingly digital and threat-filled environment. Prioritizing IT security should be viewed not as an optional expense but as a fundamental investment in the firm’s future and the trust placed in it by its clients.

Key Valuable Tables:
Summary of ABA Formal Opinions on Technology and Data Security:
Opinion Number | Title | Year Issued | Key Focus Areas | Relevance to Small Law Firms |
477R | Securing Communication of Protected Client Information | 2017 | Reasonable efforts to secure client communications, including risk assessment and potential need for encryption. | Emphasizes the importance of securing electronic communications, especially email, for sensitive client data. |
483 | Lawyers’ Obligations After an Electronic Data Breach or Cyberattack | 2018 | Proactive monitoring, incident response planning, client notification in case of a data breach. | Outlines crucial steps for preparing for, responding to, and mitigating the impact of cyberattacks. |
498 | General Guidance for Virtual Law Practices | 2021 | Application of technology competence, confidentiality, and supervision principles to virtual law practices. | Addresses security challenges specific to remote work and the use of various virtual technologies. |
512 | Ethics Guidance on a Lawyer’s Use of AI Tools | 2024 | Ethical obligations related to using generative AI, including competence, confidentiality, communication, and fees. | Provides guidance on the responsible and ethical use of AI in legal practice, including data protection. |
Common Security Controls Mandated by Insurers:
Security Control | Description | Importance for Small Law Firms | Typically Required by Insurers |
Multi-Factor Authentication (MFA) | Requires two or more verification factors to access accounts. | Significantly reduces the risk of unauthorized access. | Yes |
Endpoint Detection and Response (EDR) or Antivirus Software | Detects and prevents malware and other threats on devices. | Protects individual computers and the network from malicious software. | Yes |
Regular Data Backups | Maintaining up-to-date copies of data in a separate location. | Enables data recovery in case of loss or ransomware attack. | Yes |
Security Awareness Training for Employees | Educating staff about cybersecurity threats and best practices. | Reduces the risk of human error leading to breaches. | Yes |
Incident Response Plan (IRP) | A documented plan for handling cyber incidents. | Ensures a swift and effective response to minimize damage. | Yes |
Firewalls | Controls network traffic and blocks unauthorized access. | Essential for securing the firm’s network perimeter. | Yes |
Strong Password Policies | Rules for creating and managing complex passwords. | Prevents unauthorized access through weak or compromised passwords. | Yes |
Access Management | Limiting access to data based on user roles and needs. | Ensures only authorized personnel can access sensitive information. | Yes |
Data Classification | Categorizing data based on sensitivity to apply appropriate security controls. | Helps prioritize security efforts for the most critical information. | Yes |
eSudo is a good partner in developing and supporting long-term performance, in-office, and remote needs, cybersecurity safety, and virtual workspace to any office to the next level.


